Modern businesses rely heavily on collecting and managing client data to streamline operations and enhance customer experiences. However, because this digital goldmine has many data security and privacy challenges, you must choose the right data collection method that safeguards sensitive information and maintains trust.
Read on as we explore five options for collecting client data securely to help you determine which is right for your business.
Source: Wikimedia Commons
1. Encrypted Forms: Fortifying Data at the Source
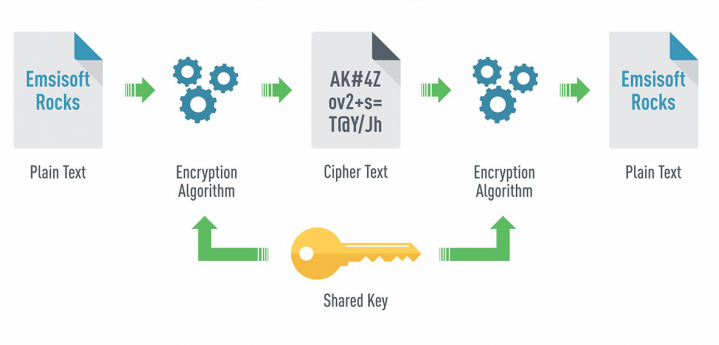
Encrypted forms are one of the most common and straightforward methods of collecting client data securely. These forms use encryption algorithms to scramble the data during transmission, rendering it exceedingly challenging for unauthorized parties to decrypt.
Implementing SSL/TLS protocols adds an extra layer of security by establishing a secure connection between the user’s device and the server. This ensures the data remains safeguarded during its journey, making interception and unauthorized access nearly impossible.
Encrypted forms are a robust first line of defense option suitable for businesses that frequently gather client information through online forms, such as contact forms, registration forms, or feedback surveys.
However, the efficacy of this method also hinges on the security of the data storage server. This highlights the importance of fortifying the transmission process and the storage infrastructure to create a comprehensive and impregnable data security strategy.
2. Tokenization: Masking Sensitive Information
Tokenization is a process that substitutes sensitive data with distinctive tokens, rendering the original information unreadable to bad actors and enhancing security by avoiding direct exposure to the original information. This method is particularly effective in scenarios that involve recurring payments or transactions.
By tokenizing payments, credit card information, or personal identifiers, businesses can reduce the risk of exposing critical data even if their systems are compromised. For eCommerce platforms and subscription-based services, tokenization is a valuable option that enhances security without hindering the user experience.
However, to fully leverage the benefits of tokenization, businesses must choose a reputable tokenization service and ensure strict adherence to industry standards.
3. Biometric Authentication: A Futuristic Approach
Biometric authentication through techniques like fingerprint scanning or facial recognition offers a cutting-edge solution to secure client data. Harnessing these unique physiological characteristics allows biometric authentication to provide an additional security layer that surpasses limitations inherent to traditional password-based systems.
Particularly advantageous for businesses focusing on mobile applications or those handling highly sensitive information, biometric authentication elevates security measures and simplifies the user experience, streamlining access while enhancing protection.
However, businesses that want to use this data collection method must stay abreast of the legal and ethical considerations surrounding biometric data collection. Compliance with privacy regulations, transparency in data usage, and the adoption of robust security measures within the system further fortify data protection.
4. Homomorphic Encryption: Securing Data in Use
Homomorphic encryption is a groundbreaking method that allows you to execute computations on encrypted data without decryption. This innovative method fundamentally transforms the traditional approach to data processing, allowing businesses to conduct computations on sensitive information without exposing it to potential threats.
Homomorphic encryption provides high security while maintaining the integrity and confidentiality of the underlying data. It is particularly relevant for businesses engaged in complex computations on client data, such as those in data analytics or machine learning applications.
The strength of homomorphic encryption lies in its ability to protect sensitive information throughout the entire computational process, from data input to analysis and output.
However, this robust security feature comes at a cost, as implementing homomorphic encryption requires substantial computational resources and specialized expertise. Businesses considering this advanced data collection and encryption technique must carefully assess their computational capabilities and the specific needs of their data-centric applications.
5. eForms for Health Data Security Compliance: A Specialized Imperative
Businesses dealing with health data must adhere to stringent security measures due to the sensitive nature of this information. Stringent access controls, restricting data access solely to authorized personnel, are essential to minimize the risk of potential breaches.
Compliance with health data regulations, notably the Health Insurance Portability and Accountability Act (HIPAA), is not merely a legal requirement but an ethical commitment to ensuring the privacy and integrity of patient information.
Businesses dealing with such data can fortify these measures by implementing secure data storage solutions, such as robust encryption protocols and secure electronic forms, to safeguard health data against unauthorized access or malicious activities.
By diligently adhering to these health data security measures, businesses can comply with regulatory standards and reinforce their commitment to maintaining clients’ trust and confidence.
Conclusion
Evaluate your business’s specific needs, stay informed about emerging data technologies, and continuously update your security measures to stay ahead in the dynamic data protection landscape.
Editorial Team
The Editorial Team at GoOnlineTools.com specializes in delivering cutting-edge information on technology.
View all postsComments 0
No comments yet. Start the conversation!